FIDO2 is an open authentication standard developed by the FIDO Alliance, that offers an enhanced level of security based on public key cryptography. It uses built-in authenticators on devices or Security keys to log users into websites securely. ADSelfService Plus uses the WebAuthn API for FIDO passkey authentication to provide secure access to protected network resources.
FIDO Passkeys offers high assurance, phishing-resistant authentication.
ADSelfService Plus currently offers FIDO passkey authentication for resources protected by browser-based MFA, like
Note: This authenticator currently does not support MFA for VPN and machine logins, as well as password resets and account unlocks via the ADSelfService Plus mobile app or the GUI login screen of Windows, macOS or Linux machines.
ADSelfService Plus offers the following types of FIDO Passkeys:
These authenticators are built into the device and are used by the platform (the OS) to verify the user's identity. Examples include Windows Hello, Android Biometrics, and Apple Touch ID/Face ID. Using ADSelfService Plus, users can utilize these authenticators to verify their identity for access to protected resources.
Platform authenticators can either be device-bound or synced across multiple devices via vendor's cloud.
Roaming passkeys are portable FIDO2-compliant Security keys like Yubikeys, Google Titan keys, etc., or the inbuilt authenticator on smartphones which can be enrolled via CDA.
Roaming authenticators can be used to verify the user's identity on any device.
Cross-Device Authentication (CDA) allows a roaming passkey on one device to be used to authenticate on another device. For example, you can use the roaming passkey on your phone to sign into ADSelfService Plus on your laptop.
Note: Security Keys do not support passkey syncing and cross-device authentication. Only a roaming smartphone can be used for CDA.
IMPORTANT NOTE: Please finalize your Access URL and Relying Party ID before enabling FIDO Passkeys.
Please ensure that you decide on the Access URL for ADSelfService Plus if your organization utilizes (or plans to utilize) Load Balanced, Highly Available or internet-facing deployments of ADSelfService Plus, which need an access URL to be configured. This is crucial because the Relying Party ID (RP ID) for FIDO Passkeys relies on the same server information as the access URL. If the access URL is modified, the FIDO RP ID will also change, resulting in the loss of enrollment data and disenrollment of all users.
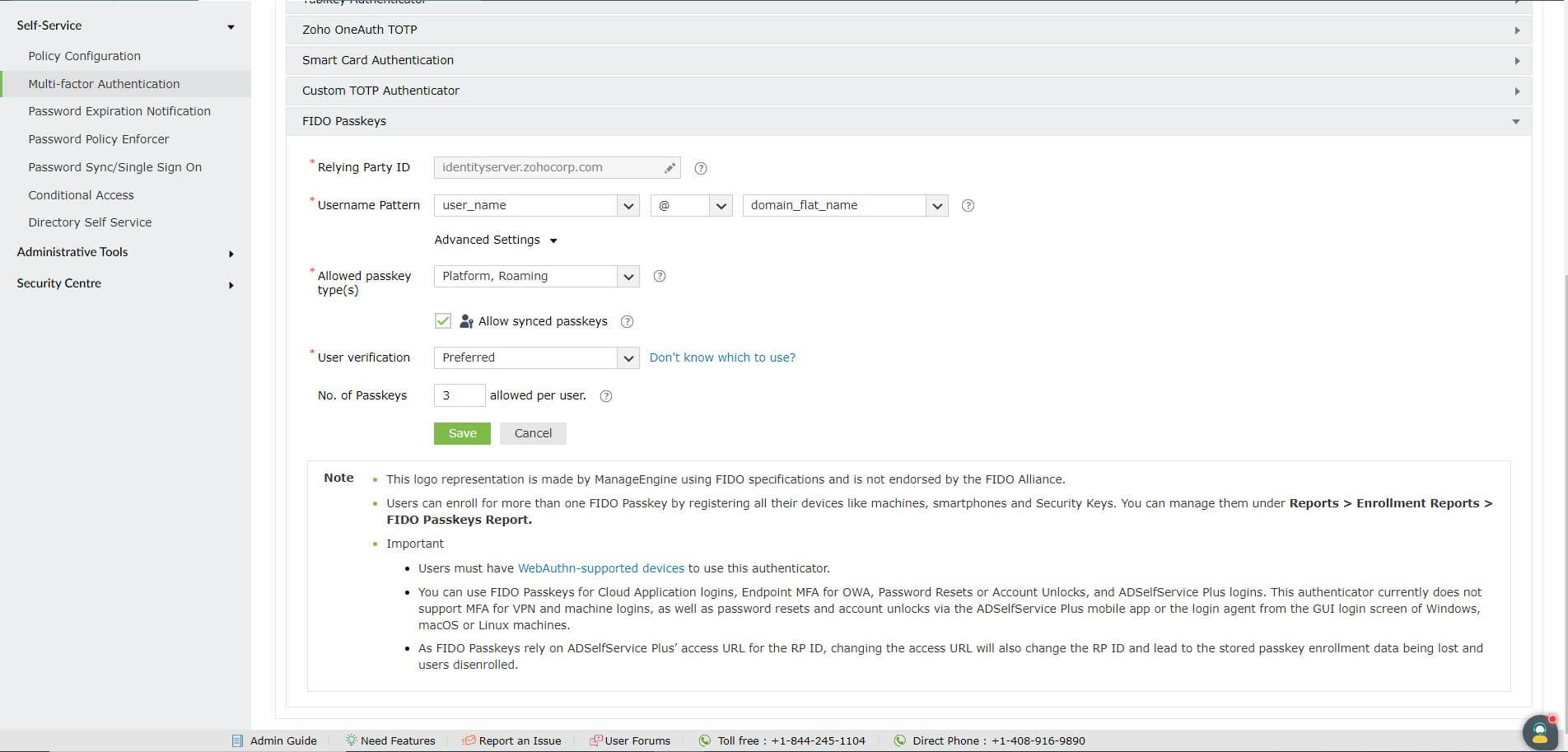
Security caution: Specifying a parent domain in the RP ID allows FIDO passkeys to be used across the domain's subdomain websites as well. So for instance, if example.com is chosen as the Relying Party ID, then FIDO passkeys registered on site1.example.com can also be used on site2.example.com or site3.example.com.
To allow FIDO Passkeys enrolled with ADSelfService Plus to authenticate only with the product, you can define the authentication scope by specifying the access URL used in ADSelfService Plus as the RP ID.
Note: If Allow synced passkeys is selected, the passkeys will be allowed to sync to the device's cloud service, allowing verification using the same passkey on the device being enrolled as well as it's synced devices.This is governed entirely by the device manufacturer's specifications and not by ADSelfService Plus.
Administrators can uncheck the Allow Synced Passkeys checkbox to block the enrollment of devices which are capable of syncing to the cloud and restrict FIDO enrollment data to only organizational devices. The authenticator on devices which mandate syncing to the cloud, like Apple devices, will be prevented from being enrolled as a FIDO passkey.
Note: If admins set the User Verification on new or existing configurations to Required, users will be prompted to provide additional user verification, such as a PIN or biometrics, after inserting their device. They will be unable to complete MFA authentication and will be locked out if secondary authentication is not set up on their devices.
The OS and browsers that support each of the following types of passkeys are as follows:
Note: Please make sure that you are using the latest versions of browsers that are not specifically mentioned by their version numbers in the following tables.
Platform authenticators can be used via either the enrolled device (device-bound passkeys) or its synced devices also (synced passkeys).
1. Device-bound passkeys:
| Windows 10+ (Windows Hello) | macOS 11+ (Touch ID) | Android 7+ (Android biometrics) | iOS 14.5+ (Face ID) | |
|---|---|---|---|---|
| Google Chrome | Yes (73+) | Yes (70+) | Yes (95+) | Yes (95) |
| Edge | Yes (79+) | Yes | Yes | Yes(95) |
| Safari | N/A | Yes (14+) | N/A | Yes (14.5) |
| Firefox | Yes (66+) | Yes | Yes (68+) | Yes (38) |
2. Synced Passkeys
| Windows 10+ (Windows Hello) | macOS 13+ (Touch ID) | Android 9+ (Android biometrics) | iOS 16.5+ (Face ID) | |
|---|---|---|---|---|
| Google Chrome | No | Yes (70+) | Yes | Yes |
| Edge | No | No | Yes | Yes |
| Safari | N/A | Yes (14+) | N/A | Yes |
| Firefox | No | Yes | Yes | Yes |
Roaming authenticators can be Security keys like YubiKeys, Google Titan keys, etc., or smartphones used for cross-device authentication (CDA).
1. Security Keys
| Windows 10+ | macOS 11+ | Linux | Android 7+ | iOS 14.5+ | |
|---|---|---|---|---|---|
| Google Chrome | Yes | Yes | Yes | Yes | Yes |
| Edge | Yes | Yes | Yes | Yes | Yes |
| Safari | N/A | Yes | N/A | N/A | Yes |
| Firefox | Yes | Yes | Yes | Yes | Yes |
2. Cross-Device Authentication (CDA) for Roaming Passkeys
CDA Client: The CDA client in a cross-device authentication flow is the device on which ADSelfService Plus is being accessed.
CDA Authenticator: The CDA authenticator in a cross-device authentication flow is the device on which the user is verifying their identity.
The supported CDA Clients and Authenticators are as follows:
| Windows 10 (Windows Hello) | Windows 11 (Windows Hello) | macOS 13+ (Touch ID) | Linux | Android 9+ (Android biometrics) | iOS 17+ (Face ID) | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| CDA Client support | CDA Authenticator support | CDA Client support | CDA Authenticator support | CDA Client support | CDA Authenticator support | CDA Client support | CDA Authenticator support | CDA Client support | CDA Authenticator support | CDA Client support | CDA Authenticator support | |
| Google Chrome | Yes (108+) | No | Yes (108+) | No | Yes (70+) | No | Yes | No | No | Yes | Yes | Yes |
| Edge | Yes (108+) | No | Yes (108+) | No | Yes | No | Yes | No | No | Yes | Yes | Yes |
| Safari | N/A | N/A | N/A | N/A | Yes (14+) | No | N/A | N/A | N/A | N/A | Yes | Yes |
| Firefox | No | No | Yes | No | Yes | No | No | No | No | Yes | Yes | Yes |
To enroll for FIDO Passkeys, the user needs to access the self-service user portal, click Enrollment > FIDO Passkeys and follow the applicable steps. The same procedure should be followed for all devices or platforms that the user wants to enroll as a passkey.
You can find the detailed enrollment steps here.
Note: Enrollment for FIDO Passkeys is not possible in bulk by importing data from a CSV file or an external database, or via a login script.
Enrollment for FIDO Passkeys is not possible from AD360's Apps Pane. Users will need to directly access the ADSelfService Plus url to enroll for FIDO Passkeys.
Platform Authenticators: Platform authenticators (Device's Built-in Passkeys) can be used for MFA only on the enrolled device. If the user tries to authenticate with a platform authenticator on a non-enrolled device, MFA will fail and the user will not be able to access the resource unless backup codes are enabled in your organization, and they have backup codes for their account.
Synced passkeys: Synced passkeys enables the sharing of a single enrollment across all devices that are synced to the cloud; i.e., when passkeys are synced, users can authenticate using the same passkey on the enrolled device or any of its synced devices.
Note: The FIDO Passkeys Report will only show the enrollment on the specific device that was enrolled, and not on its synced devices.
Roaming passkeys: Authentication using Security keys can be done by accessing the ADSelfService Plus web portal from a device on which the key can be plugged in, or connected via NFC or BLE.
Authenticators like Android Biometrics or Apple Touch ID/Face ID on smartphones which are not used to access the ADSelfService Plus portal, can also be enrolled as Roaming passkeys and used for CDA via methods like QR-code scanning with Bluetooth Low Energy (BLE).
Note: A single Security key can be enrolled as a passkey for multiple users. Multiple Security keys can also be enrolled for a single user account. Similarly, the same smartphone can be enrolled as a Platform (Device's built-in) Authenticator or a Security key for all the users who have enrolled for that phone's biometric authentication.
However, the same smartphone cannot be registered as both a built-in authenticator as well as a Security Key for the same user. Each device can be registered as only one type of authenticator per user. If a user attempts to access the ADSelfService Plus end-user portal on a smartphone that has already been registered to them as a Security key (roaming authenticator), they need to select 'Security Key' as the passkey type to authenticate and confirm their identity on the same smartphone. They cannot choose 'Device Built-in Authenticator' even though they are both accessing and authenticating to the portal on the same device.
Copyright © 2024, ZOHO Corp. All Rights Reserved.