Updating Windows cached credentials
When users in an AD environment log into their Windows machines from within the organizational network, their login details are saved in the local cache on their machines. This allows them to log in again with their Windows password even if they are away from the corporate network, as the credentials will be verified against their local cache instead of AD. However, if they forget their password or their cached password expires while users are not connected to the corporate network, they will neither be able to log in nor receive prompts to update their passwords. Even if their admin resets their password remotely, it will not get synced with the cache when the machine is away from the organizational network, and the users will be locked out.
ADSelfService Plus solves this by adding a Reset Password/Unlock Account link directly to the Windows login screen. To reset their passwords, users are required to click the link and prove their identity through any one of the enforced authentication methods, such as: Hardware and Software Tokens, Biometric Authentication, or Push Authentication. Once a user’s identity is successfully verified, they will be allowed to reset their forgotten or expired AD domain passwords.
Important:
- The ADSelfService Plus Windows Login Agent is required for this feature to work. You can find steps to install the agent here.
- Updating cached credentials is supported only for Windows.
- Users must be enrolled in ADSelfService Plus to utilize the self-service password reset and self-service account unlock capabilities.
- Enrollment is a one-time process where users enter their mobile number and email address, set answers to security questions, or provide other details in ADSelfService Plus in order to register for self-service password management. Learn how to enroll users.
Updating the local cached credentials on Windows machines can be achieved:
- Through a VPN client
- Without using a VPN
Updating cached credentials through a VPN client
The ADSelfService Plus login agent uses a command-line interface (CLI) to initiate a connection with the integrated VPN. Any VPN provider that supports a CLI with LocalSystem account privileges can be used for cached credentials update. These VPN CLI commands will be used by ADSelfService Plus to automatically connect to AD during the Password Reset and Cached Credential Update operations.
Supported VPN clients
- Fortinet
- Cisco IPSec
- Cisco AnyConnect
- Windows Native VPN
- SonicWall NetExtender
- Checkpoint EndPoint Connect
- SonicWall Global VPN
- OpenVPN
- Custom VPN
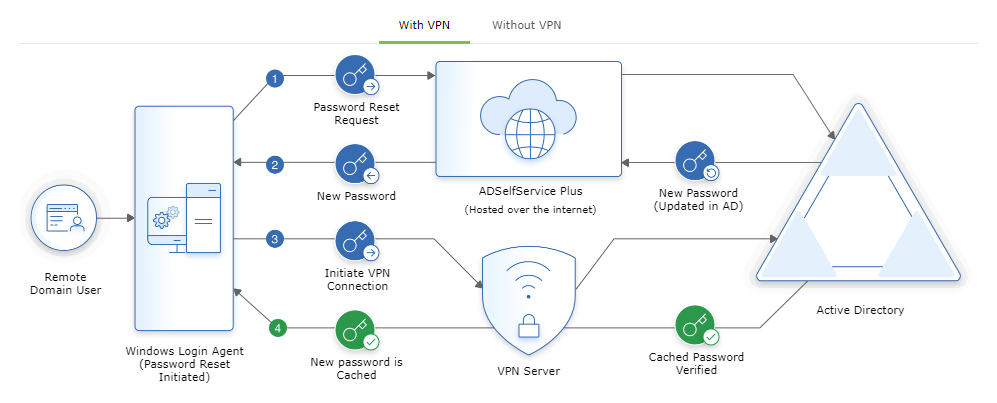
Process flow
If Update cached credentials through a VPN client is enabled,
- The user's identity is verified through MFA, and the reset password request is sent to ADSelfService Plus, which updates the new password in AD.
- The new password is sent to the Windows Login Agent on the user's machine.
- The login agent automatically establishes a secure connection with AD through the VPN connection commands configured and initiates a request for updating the local cached credentials.
- The request is successfully approved by AD, and the cached credentials are automatically updated in the local cache on the user's Windows machine .
Configuring cached credential update through a VPN
Prerequisites
- You must have installed a VPN client that supports a CLI with LocalSystem account privileges on every user's machine.
- Please be prepared with a service account if:
- Your organization has mandated MFA for end-user VPN connections, or
- A shared account is used for all the VPN connections initiated by your organization users.
Note: By default, VPN connections to update the local cache will be initiated with the credentials of the end-user who initiated the password reset.
Configuration steps
- Log into ADSelfService Plus with administrator credentials.
- Navigate to Configuration > Administrative Tools > GINA/Mac/Linux (Ctrl+Alt+Del).
- Click Windows Cached Credential Update.
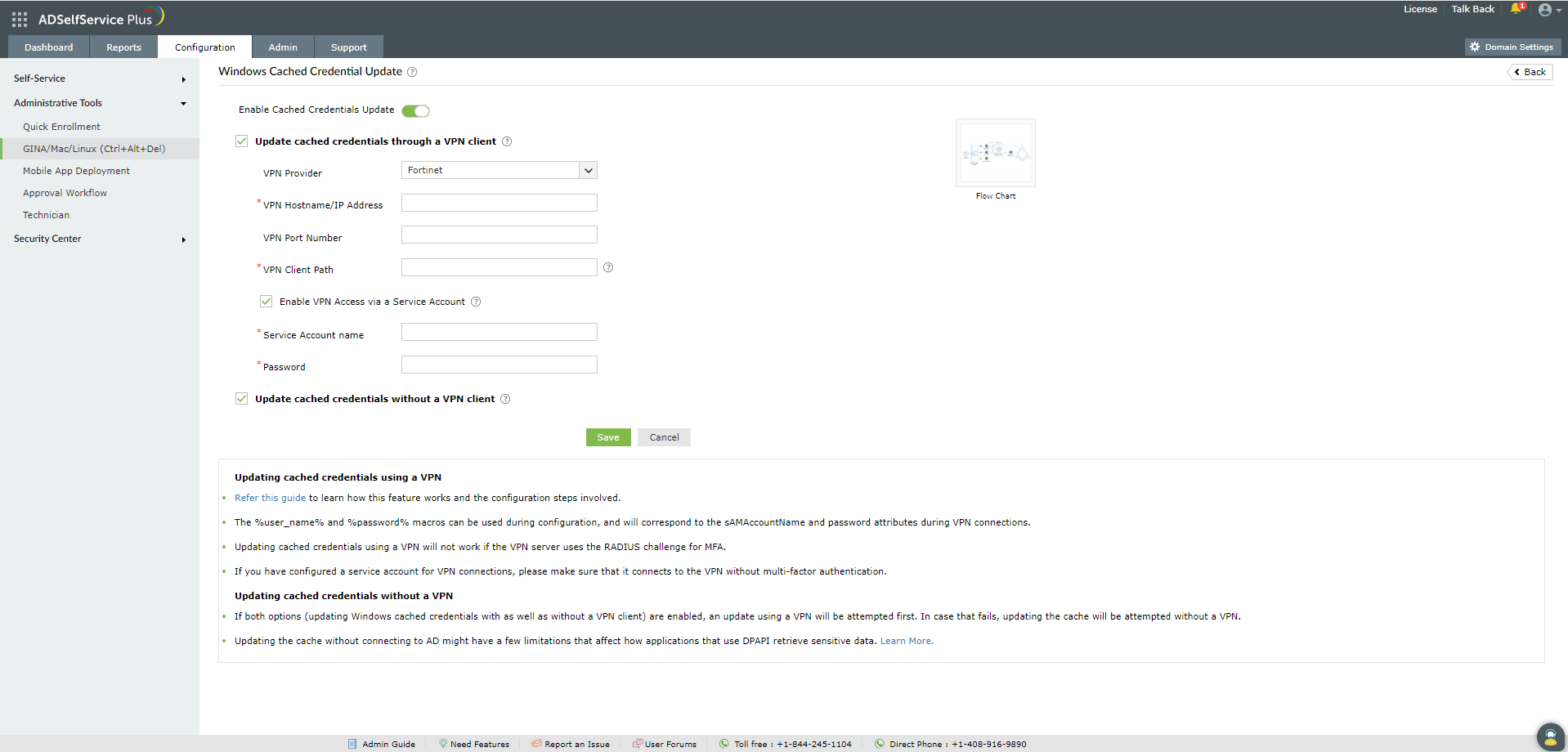
- Set the toggle button to Enable Cached Credential Update.
- Select Update cached credentials through a VPN client.
- Select the VPN Provider from the drop-down list.
- Enter the VPN Hostname/IP address and VPN Port Number in their respective fields.
- In the VPN Client Path field, enter the full path to where the VPN client is installed on the users' machines. For example,
C:\ProgramFiles\Fortinet\FortiClient\FortiClient.exe
- If you want to use a service account for VPN connections, select Enable VPN Access via a Service Account and enter the service acount's credentials.
Here are the client locations for the VPN providers supported out of the box in ADSelfService Plus:
- Cisco AnyConnect: C:\ Program Files (x86 )\Cisco\Cisco AnyConnect\vpncli.exe
- SonicWall Global VPN: C:\Program Files (x86)\SonicWall\SonicWall Global VPN\swgvc.exe
- Fortinet VPN: The appropriate version of the VPN client file (FortiSSLVPNClient.exe) must be downloaded from the Fortinet support portal and installed on users' machines. To download the VPN client file (FortiSSLVPNClient.exe), log into the Fortinet support portal and navigate to Firmware Downloads > FortiClient > select_your_VPN_version > FortinetClientTools.zip. Click on HTTPS to download the ZIP file. Unzip and extract the FortiSSLVPNClient.exe file (you can find it within the SSLVPNcmdline folder) to a location accessible to the ADSelfService Plus Windows Login Agent. The location where the FortiSSLVPNClient.exe file has been installed must be mentioned as the VPN Client Path. Example:
C:\FortiClient\FortiSSLVPN\x86\FortiSSLVPNClient.exe
- Check Point VPN: C:\Program Files (x86)\CheckPoint\Endpoint Connect\trac.exe
- SonicWall NetExtender: C:\Program Files (x86)\Sonicwall\SSL-VPN\NetExtender\necli.exe
- OpenVPN: C:\Program Files (x86)\Sophos\Sophos ssl client\bin\openvpn.exe
- Cisco IPSec: C:\Program Files (x86)\Cisco\Cisco IPSec\vpnclient.exe
The VPN client location has to be uniformly maintained on all user machines. If using a custom VPN provider, please contact your VPN provider's support team to know the name of the client used for command-line interface and mention its location as the client location.
For Custom VPN, macros (%user_name%, %password%, etc.) can be used in the VPN Connect/Disconnect Command. (Note: The syntax for the VPN Connect/Disconnect Command varies depending on the VPN provider used.)
Example: connect -s adsspvpn -h %servername%:%portno% -u %user_name%:%password%
- Click Save.
VPN provider-specific settings
These are settings specific to VPN providers that let admins have granular control over the VPN connections. The provider-specific settings for VPNs supported by ADSelfService Plus are outlined below.
Fortinet
- Protocol: L2TP (Layer 2 Tunneling Protocol). Other protocols are not supported as of now.
- Supported macro(s): %user_name%, %password%, %servername% and %portno%
Cisco Anyconnect VPN
- Unsupported features: The Accept Disclaimer banner.
- VPN Group Name: When connecting to Cisco Anyconnect VPN using the command line, if the prompt asks you to enter the VPN Group Name as a number from the given list ( Eg: 1 - VPN admins, 2 - VPN users), kindly enter the same number as in the VPN Group Name field in the ADSelfService Plus admin portal.
Windows Native VPN
- Supported protocol: L2TP (Layer 2 Tunneling Protocol). Other protocols are not supported as of now.
- Pre-shared key: Enter the pre-shared key used for an L2TP connection.
Open VPN
- Sample Connect command: --config "<Full_path_to_the_o.vpn_file>" --auth-user-pass %tempFile%
You will need to replace <Full_path_to_the_o.vpn_file> with the full path to the .ovpn file located on the machine. The user or service account's credentials will be entered in a temporary file created during the login process. The %tempFile% macro will be replaced with this filename during the VPN connection, and the password will be updated in the cache. Learn more.
Note: After updating the new password in cache, the VPN will be disconnected and the temporary file will be deleted automatically, thus protecting the user account's credentials.
Custom VPN
- Sample connection command: -t vpn.selfservice.com -u john -i allow -U -P autologin -m other connect
- Supported macro(s): %user_name%, %password%, %servername% and %portno%
VPN Macros available in ADSelfService Plus
- %user_name% - will be replaced by user's sAMAccountName or service account's user name
- %password% - will be replaced by user's password or service account's password
- %servername% - will be replaced by the value of VPN HostName/IP
- %portno% - will be replaced by the value of VPN port number
Note: All sensitive information like the service account's credentials or the pre-shared key used for Windows Native VPN will be stored in the ADSelfService Plus database as an encrypted string, which will be sent to the Windows login agents dynamically when requested. It can be decrypted only by a valid Windows login agent.
The VPN connection established will be disconnected automatically after updating the cache with the new password, thus ensuring that the VPN connection is not misused to access any resource.
Updating cached credentials without a VPN client
Cached credentials can be updated without a VPN if your organization does not have VPN infrastructure or uses a VPN vendor not supported by ADSelfService Plus.
Process flow
If Update Cached Credentials without a VPN client is enabled,
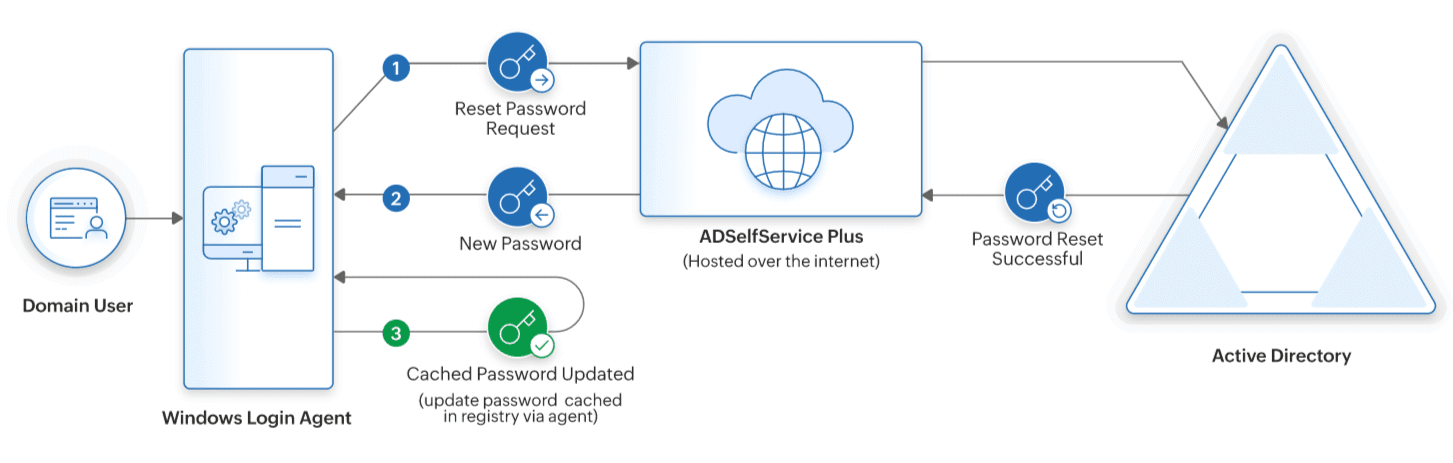
- The user's identity is verified through MFA and the Reset Password request is sent to ADSelfService Plus, which updates the new password in AD.
- After the new password is updated in AD, the local cache on users' machines is automatically updated with the new password.
Configuration steps
- Log into ADSelfService Plus with administrator credentials.
- Navigate to Configuration > Administrative Tools > GINA/Mac/Linux (Ctrl+Alt+Del).
- Click Windows Cached Credential Update.
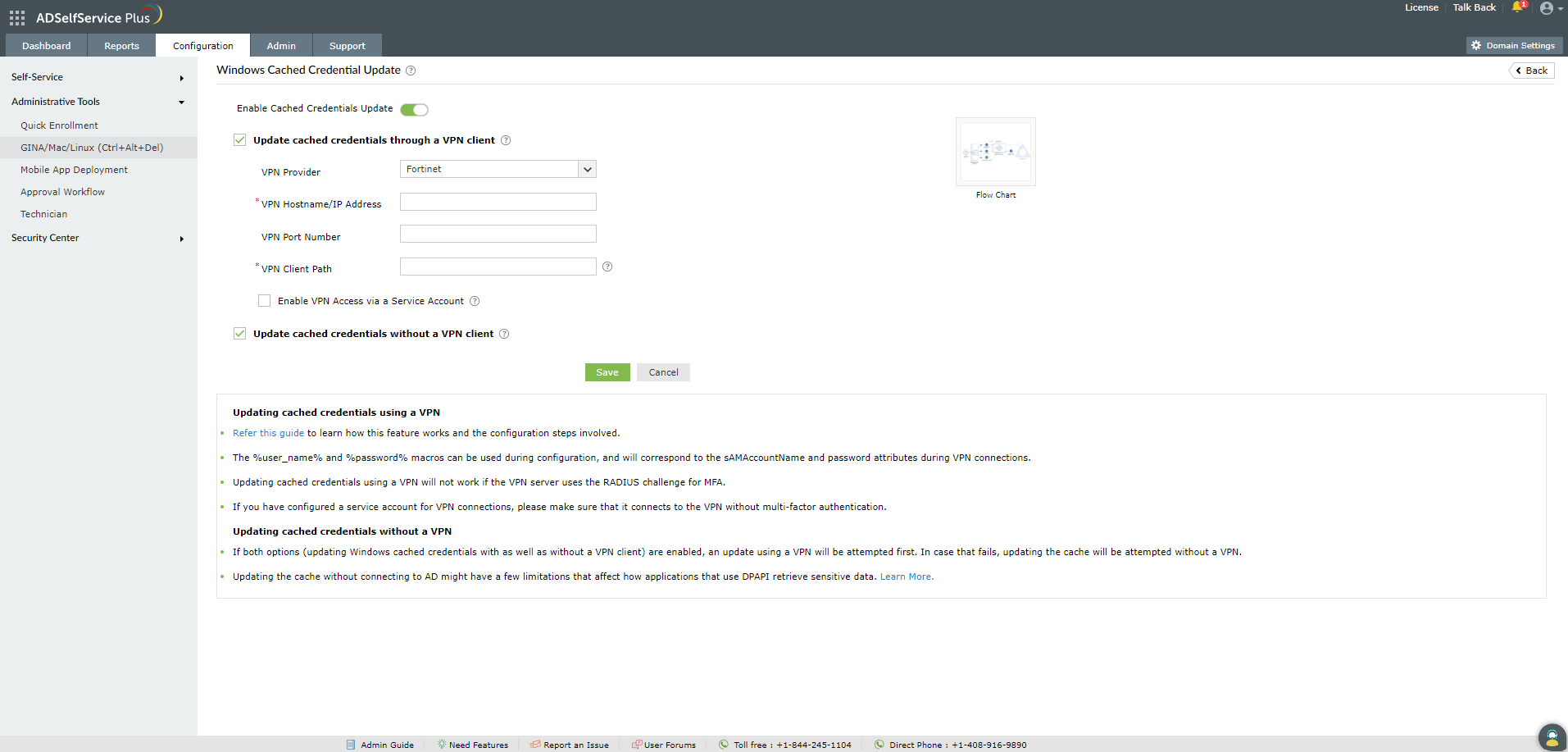
- Set the toggle button to Enable Cached Credential Update
- Select Update cached credentials without a VPN client
- Click Save.
Note: If both options (updating Windows cached credentials through as well as without a VPN client) are enabled, an update using a VPN will be attempted first. In case that fails, update of the cached credentials will be attempted without a VPN.
Updating the cache without connecting to AD through a VPN might have a few limitations that affect how applications retrieve sensitive data using DPAPI. This includes applications that use passwords and form auto-completion data, such as Internet Explorer, Yandex, and Google Chrome, network passwords stored in the Credential Manager, and private keys for Encrypting File System (EFS), SSL/TLS in Internet Information Services.
For instance, passwords that are saved on the Chrome browser are stored and retrieved using DPAPI, which requires the client to have connected to AD while updating the cached password. If the cache is updated without a VPN connection to AD, Chrome will not be able to retrieve the stored user information until the machine next connects to AD.
We recommend that you choose the Update cached credentials without a VPN client option only if your organization does not have a VPN provider supported by ADSelfService Plus for cached credential update.
Updating Cached Credentials without a VPN is supported only on Windows servers running Windows Server 2008 R2 and later, and on Windows clients running Windows 7 and later.