The following errors may arise during the installation of the GINA login agent, follow the solutions provided to resolve them:
Couldn't Start Remote Service. Overlapped I/O operation is in progress.
Multiple connections to a server or shared resource by the same user.
Error in security-core.js. The user will encounter a pop-up that displays the script error message.
When a user tries to log in to their machine, there is a delay in the loading of the GINA component.
Why does the user have to perform online MFA sometimes even after trusting their device or browser?
Why is the display language set in the ADSelfService Plus portal not reflected during Offline MFA?
'RemoteExecM1.exe' is not recognized as an internal or external command, operable program or batch file.
This error occurs if the RemoteExecM1.exe file, which is used to install the login agent in remote machines, has been flagged and deleted by the antivirus software. To resolve this issue:
Could not Install Client Software
This error occurs because of a network timeout while installing the client software. Make sure the network connection is re-established and try to install the software again.
Initiating Connection to Remote Service Failed
This error could occur if the target computer could not be contacted. To prevent this:
Couldn't connect to the machine, ADMIN$.Access is denied
This error may occur because admin share has not been enabled in the client computer. To resolve this issue:
Logon Failure: The target account name is incorrect.
This error message can occur if two computers have the same computer name. One computer is located in the child domain; the other computer is located in the parent domain.
Logon failure: unknown user name or bad password.
This error message occurs when admin share might not be enabled in the client computer. To resolve this issue:
Couldn't Start Remote Service. Overlapped I/O operation is in progress.
The Remote service couldn't be started either because the copy was blocked by antivirus or because the service couldn't be started automatically. To prevent this:
Another version of this product is already installed.
This error occurs when another version of this login agent is already installed in the remote machine. To prevent this, uninstall the existing client software from this machine.
Another installation is already in progress.
This error occurs when another installation is already in progress. To prevent this, try to install the client software after a few minutes.
Could not connect to the machine.
This error could occur if the target computer could not be contacted. To prevent this:
Network path not found/Invalid Credential.
This error could occur if the target computer could not be contacted. To prevent this:
Couldn't copy ADSelfServicePlusClientSoftware.msi
This error occurs because the ADSelfService Plus server has insufficient privileges to access the client machine. To prevent this:
Multiple connections to a server or shared resource by the same user.
This error occurs when other applications or processes are using the same user account used by ADSelfService Plus to try and connect to the remote machine in which the login agent is to be installed. To resolve this issue:
Error in security-core.js. The user will encounter a pop-up that displays the script error message.
Probable causes:
Solution:
A blank screen appears when the user tries to authenticate using Windows MFA or perform a self-service action such as password reset or account unlock.
Probable cause: Cookies are not enabled in Internet Explorer on the user's system.
Solution: Follow the steps here to enable cookies in Internet Explorer.
A blank screen appears during the endpoint MFA process.
Probable cause: The ADSelfService Plus product URL is not added as a trusted site in Internet Explorer.
Solution: Follow the steps here to add the ADSelfService Plus URL to the list of trusted sites in Internet Explorer.
When a user tries to log in to their machine, there is a delay in the loading of the GINA component.
Probable cause: The user is using a self-signed certificate.
Solution: Disable certification revocation, or the act of invalidating a TLS/SSL certificate before its scheduled expiration date. There are two ways to do this.
Method 1: Adding registry values
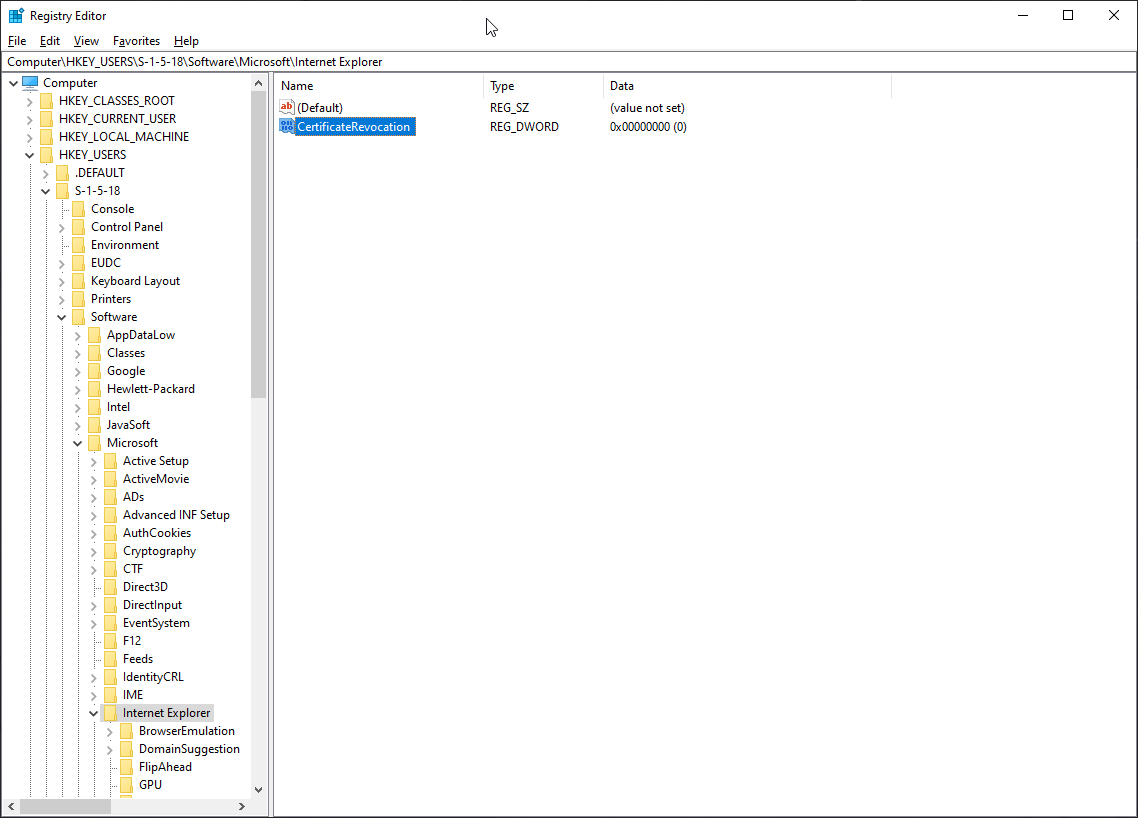
Method 2: Changing settings in Internet Explorer
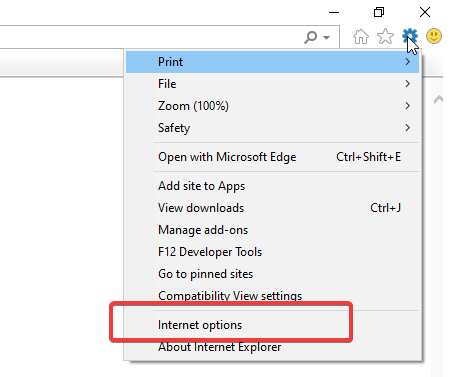
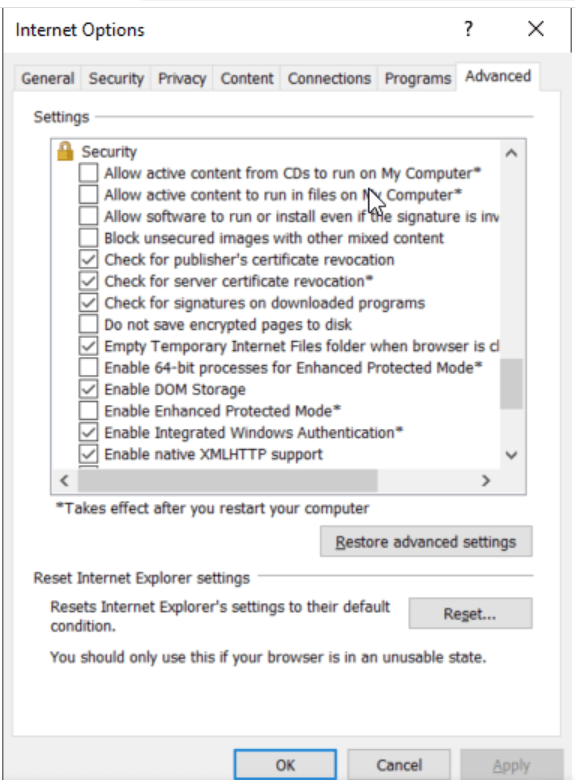
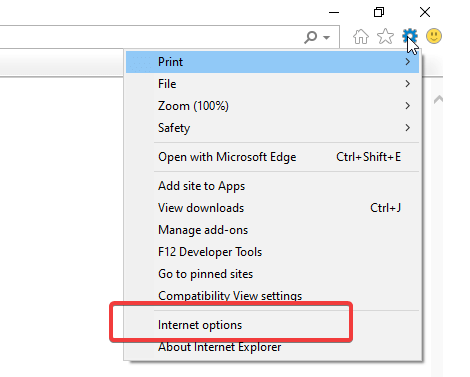
Solution: Enabling cookies in Internet Explorer on the user's system
Verify if cookies are enabled in Internet Explorer on the user's system. If they’re not, enable cookies by following the steps below:
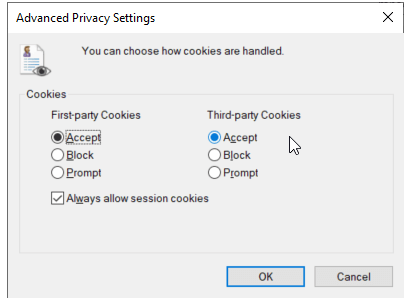
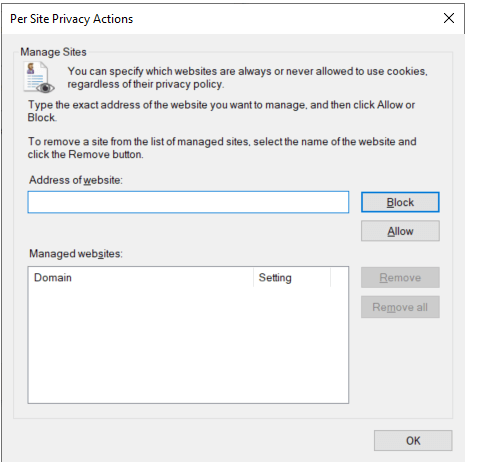
Solution: Adding the ADSelfService Plus URL to intranet/trusted sites
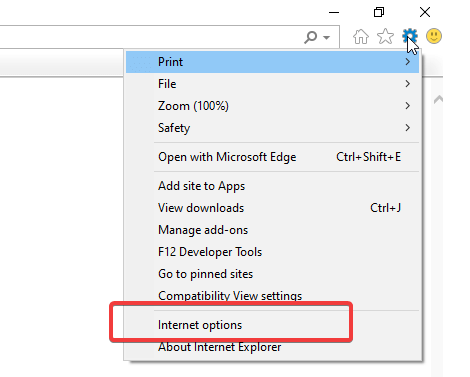
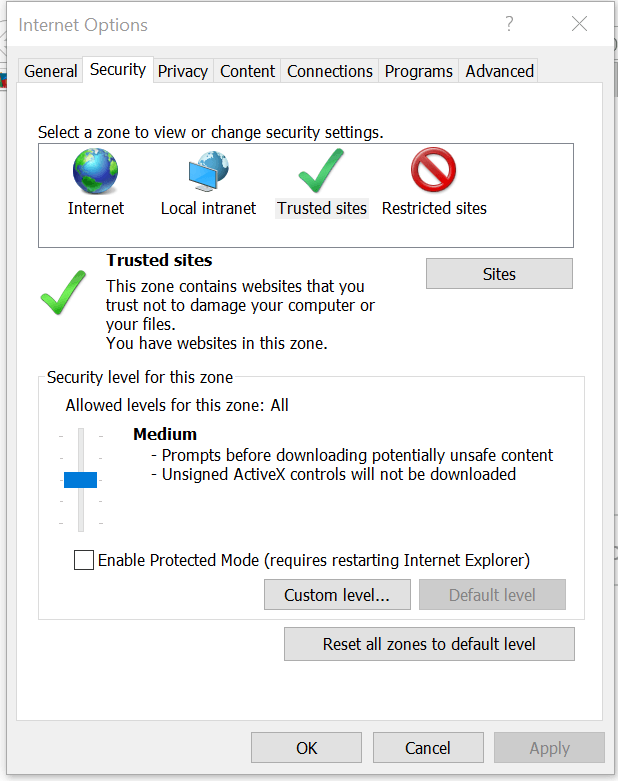
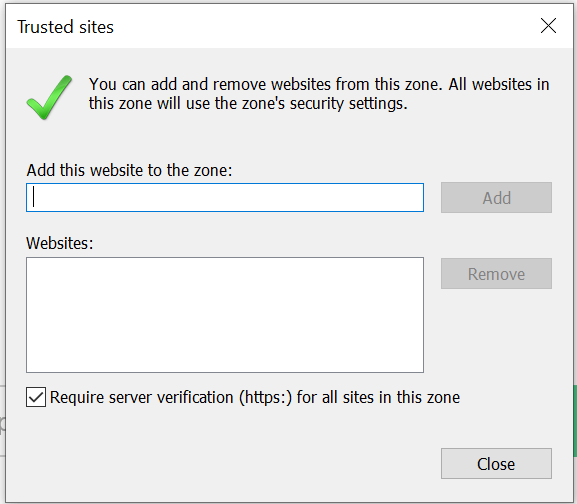
These steps should ensure that there are no further GINA loading issues.
Cause: User account does not have sufficient privilege over the object.
Solution:
Cause: PAExec is being blocked by the firewall or antivirus software.
Solution: Change your antivirus and firewall settings to allow the PAExec service.
Cause: The WMI repository may be corrupted.
Solution: To resolve the corruption of WMI repository, follow the steps in this link.
Work around:
Cause 1: The login name or password provided for scanning is invalid in the workstation.
Solution: Check if the login name and password are entered correctly.
Cause 2: The user does not have remote access to the computer through the Distributed Component Object Model (DCOM).
Solution:
The user should now have remote access to the computer through DCOM.
Cause 3: DCOM may not be configured to allow a WMI connection.
Solution: If the DCOM in the machine is not configured to allow a WMI connection, then follow the below steps in the machine that needs to accept WMI connection.
Cause 4: The Remote DCOM option is disabled in the remote workstation.
Solution: Check if Remote DCOM is enabled in the remote workstation. If not, follow the steps below to enable it:
Cause 5: The user account is invalid in the target machine.
Solution: Check if the user account is valid in the target machine by opening Command Prompt, and execute the following commands:
net use \<RemoteComputerName>C$ /u:<DomainNameUserName> "<password>"
net use \<RemoteComputerName>ADMIN$ /u:<DomainNameUserName> "<password>"
If these commands show any errors, the provided user account is not valid on the target machine.
Cause 6: The user name provided for scanning does not have sufficient access privileges to perform the scanning operation. This user may not belong to the administrator group for this device machine.
Solution: Move the user to the Administrator Group of the workstation or scan the machine using an administrator (preferably a domain administrator) account.
Solution: Move the user to the Administrator Group of the workstation or scan the machine using an administrator (preferably a domain administrator) account.
Cause 7:A firewall is configured on the remote computer. Such exceptions mostly occur in Windows XP (SP 2) when the default Windows firewall is enabled.
Solution: Disable the default Firewall in the Windows XP machine:
If the firewall cannot be disabled, launch Remote Administration for administrators on the remote machine by executing the following command in Command Prompt:
netsh firewall set service RemoteAdmin
After scanning, you can disable Remote Administration using the following command:
netsh firewall set service RemoteAdmin disable
Cause 8: WMI is not available in the remote Windows workstation. This happens in Windows NT. Such error codes might also occur in higher versions of Windows if the WMI components are not registered properly.
Solution: Install WMI in the remote workstation. Refer to these steps for help.
If the WMI Components are not registered, register the WMI DLL files by executing the following command in the command prompt: winmgmt /RegServer
Cause 9: There is some internal execution failure in the WMI service (winmgmt.exe) running in the device machine. The last update of the WMI Repository in that workstation could have failed.
Solution:
Restart the WMI service in the remote workstation:
Cause: The Remote Procedure Call (RPC) port of the machine is blocked by the firewall.
Solution: Change the setting in your firewall to allow RPC ports.
Cause: The Win32_Product class is not installed in Windows 2003 Server by default.
Solution: To add the Win32_Product class, follow the steps below:
The multiple reasons for this issue are listed below along with the solution:
Solution: Make sure offline MFA has been enabled for the self-service policy the users belongs to. If the user belongs to multiple self-service policies, make sure the self-service policy with offline MFA enabled has the highest priority.
Solution: Ensure the user has enrolled their machine for offline MFA. Enrollment could even be enforced by enabling the Force user to enroll their device for offline MFA after successful online authentication setting for the self-service policy the user belongs to. The user and their enrolled machine will be listed in the Offline MFA Enrollment Report if successfully enrolled.
Solution: Follow these steps to enable Machine-based MFA for logins and peripheral actions such as User Account Control (UAC) prompts, system unlocks, and RDP server-side authentication using these steps. After enabling MFA, run the customization scheduler to update these changes across all the user machines.
Reach out to our support team if this issue persists even after implementing this solution.
Probable cause: The OTP generated during the offline MFA process by the software or hardware TOTP authenticator is rendered invalid if the user machine and the mobile device generating the OTP don't have their times in sync.
Solution: Ensure the mobile device and the machine follow the correct time.
Solution: Check the values of the Manage MFA drop-down (Configuration > Administrative Tools > GINA/Mac/Linux (Ctrl+Alt+Del) > GINA/Mac/Linux Installation > Installed Machines). If this setting is set to Enforce, access will be denied regardless of other settings. Settings can be configured to require the user to complete online MFA, as well as to encourage or require enrollment of their machine for offline MFA.
Solution: Check the value of the Skip MFA when the ADSelfService Plus server is down or unreachable setting (Configuration > Self-Service > Multi-Factor Authentication > Advanced Settings > Endpoint MFA > Machines Login MFA() If this setting is not enabled, access will be denied. Settings can be configured to require the user to complete online MFA, as well as to encourage or require enrollment of their machine for offline MFA.
To change the outcome according to your requirements, set the value of these settings appropriately and run the customization scheduler to update the changes across all user machines. The scheduler will reflect changes only on login agents installed via the admin portal, or have remote registry services enabled.
Reach out to our support team if this issue persists even after implementing this solution.
Probable cause: The user is able to perform offline MFA until the disenrollment data is updated on the specific machine.
Solution: The disenrollment data will be updated during the next successful online MFA by any user in the specific machine.
Probable causes:
Probable cause: The display language set via the ADSelfService Plus portal is extended only to UI elements run by the server, and so only some parts of the login agent are dependent on this setting. The other parts, including features like offline MFA and Password Policy Enforcer are dependent on the welcome screen display language settings (Start > Settings > Time & Language > Administrative language settings > Welcome screen and new user accounts > Copy settings > Welcome screen display language).
Solution: Learn how to customize the display language for the offline MFA feature here.
Cause: The built-in Windows login screen timeout period for authentication is shorter than the time required to complete MFA.
Solution: The Windows login screen timeout period can be changed in the registry settings. The default timing upon installation of login agent version 6.7 and above is 3,00,000 ms (5 min). If the timeout period is already set in the registry, installing the login agent won't modify the existing value. The admin can change the value manually using these steps:
Copyright © 2026, ZOHO Corp. All Rights Reserved.