MFA Usage Audit Report
ADSelfService Plus offers MFA security for various endpoints and self-service password reset and account unlock actions. MFA can be utilized through both workstations and mobile devices.
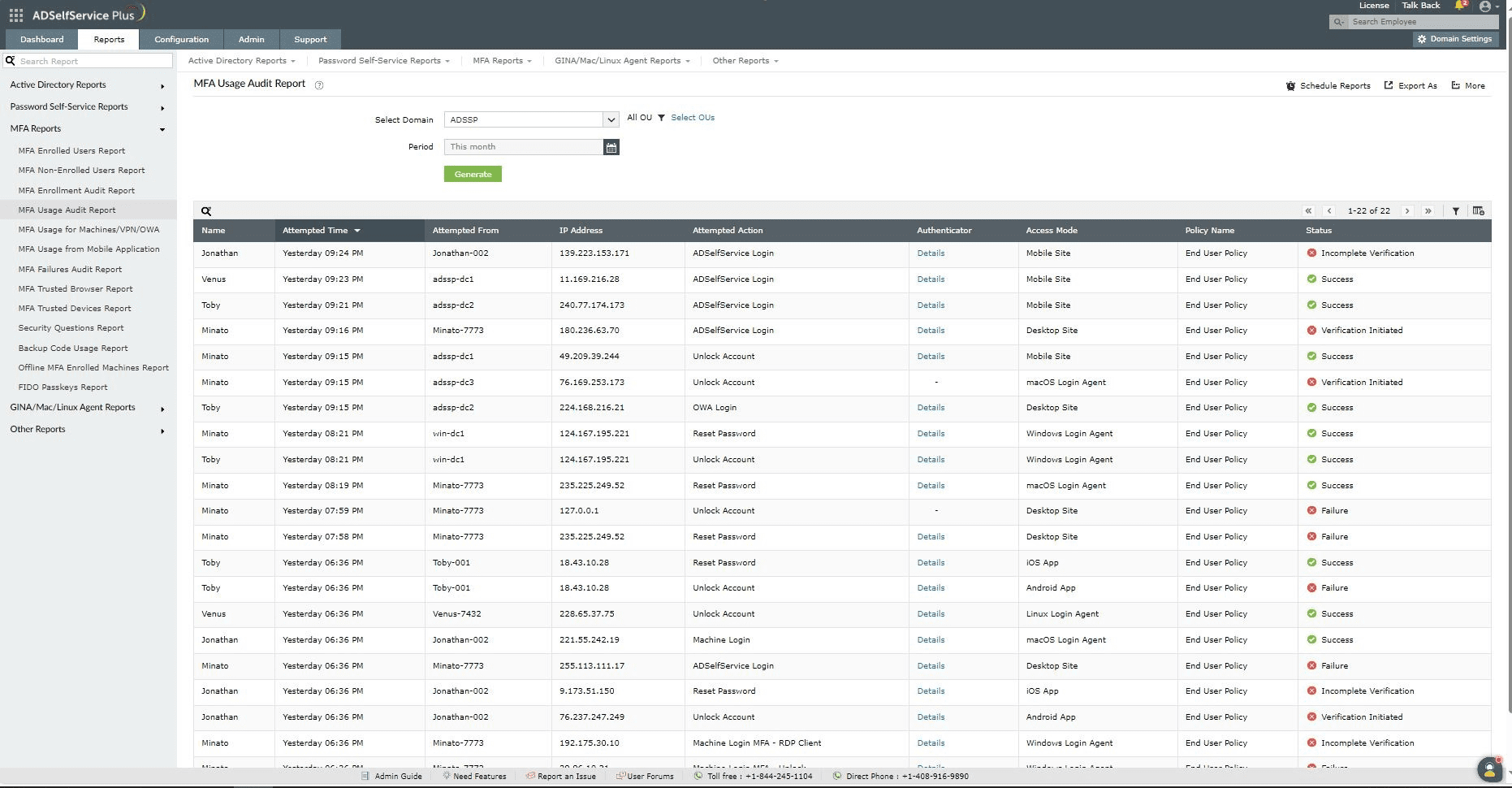
The MFA Usage Audit Report displays details of every MFA action in ADSelfService Plus. The information presented in this report includes the username, the time MFA was attempted, the module from which the MFA action was initiated, the type of endpoint used for the MFA attempt, the IP address of the machine, and the status of each MFA attempt.
Report generation
You can generate the MFA Usage Audit Report by following these steps:
- Log into the ADSelfService Plus admin portal with Administrator or Operator privileges and navigate to Reports > MFA Reports > MFA Usage Audit Report.
- Specify the domain using the Select Domain option.
- Specify OUs using the Select OUs option, if needed.
- The Period drop-down menu can be used to specify the time period for which to generate the reports. Options include Today, Yesterday, Last 7 days, Last 30 days, This month, and Custom Period.
- Click Generate.
The Status column displays if the MFA status of each attempt is a Success or a Failure. Incomplete verification attempts are also displayed. Click on Details in the Authenticator column to display all the authenticators used during every MFA attempt, including each of their MFA statuses.
Report customization
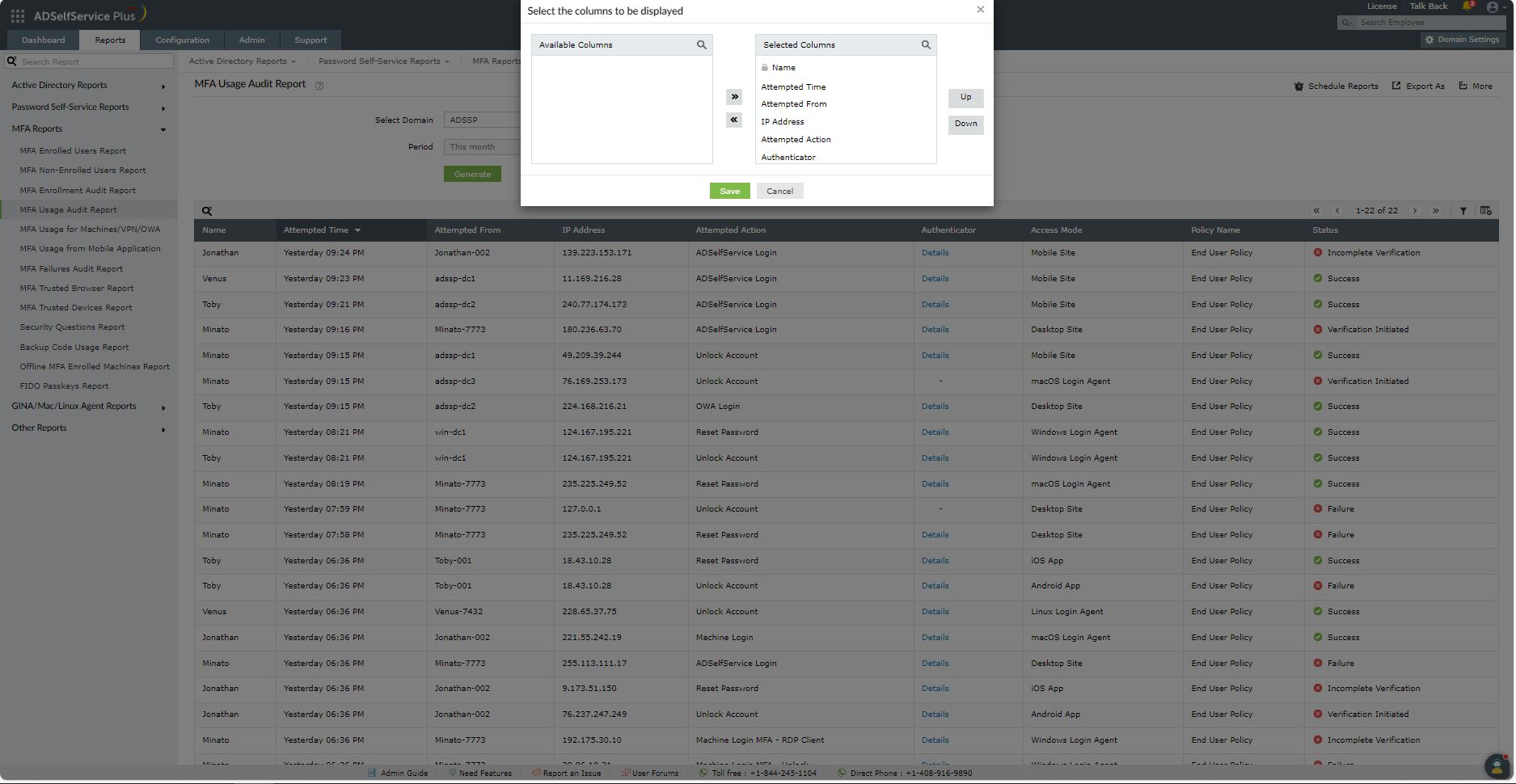
- Adding or removing columns: To add or remove columns, click on the Add/Remove Columns[
 ] option at the far right of the report. In the Select the columns to be displayed pop-up that appears, select the required fields under Available Columns and click on the right arrow [>>] to move it to the Selected Columns. To remove columns, select the unused fields under Selected Columns and click on the left arrow [<<] to move it to Available Columns.
] option at the far right of the report. In the Select the columns to be displayed pop-up that appears, select the required fields under Available Columns and click on the right arrow [>>] to move it to the Selected Columns. To remove columns, select the unused fields under Selected Columns and click on the left arrow [<<] to move it to Available Columns.
- Ordering the columns: The columns' positions can also be altered by selecting a value under Selected Columns and using the Up and Down options to change its position.
Advanced filtering
- Once the report is generated, the entries can be narrowed-down based on the following parameters by clicking on the Advanced Filter [
 ] icon at the far right of the report
] icon at the far right of the report
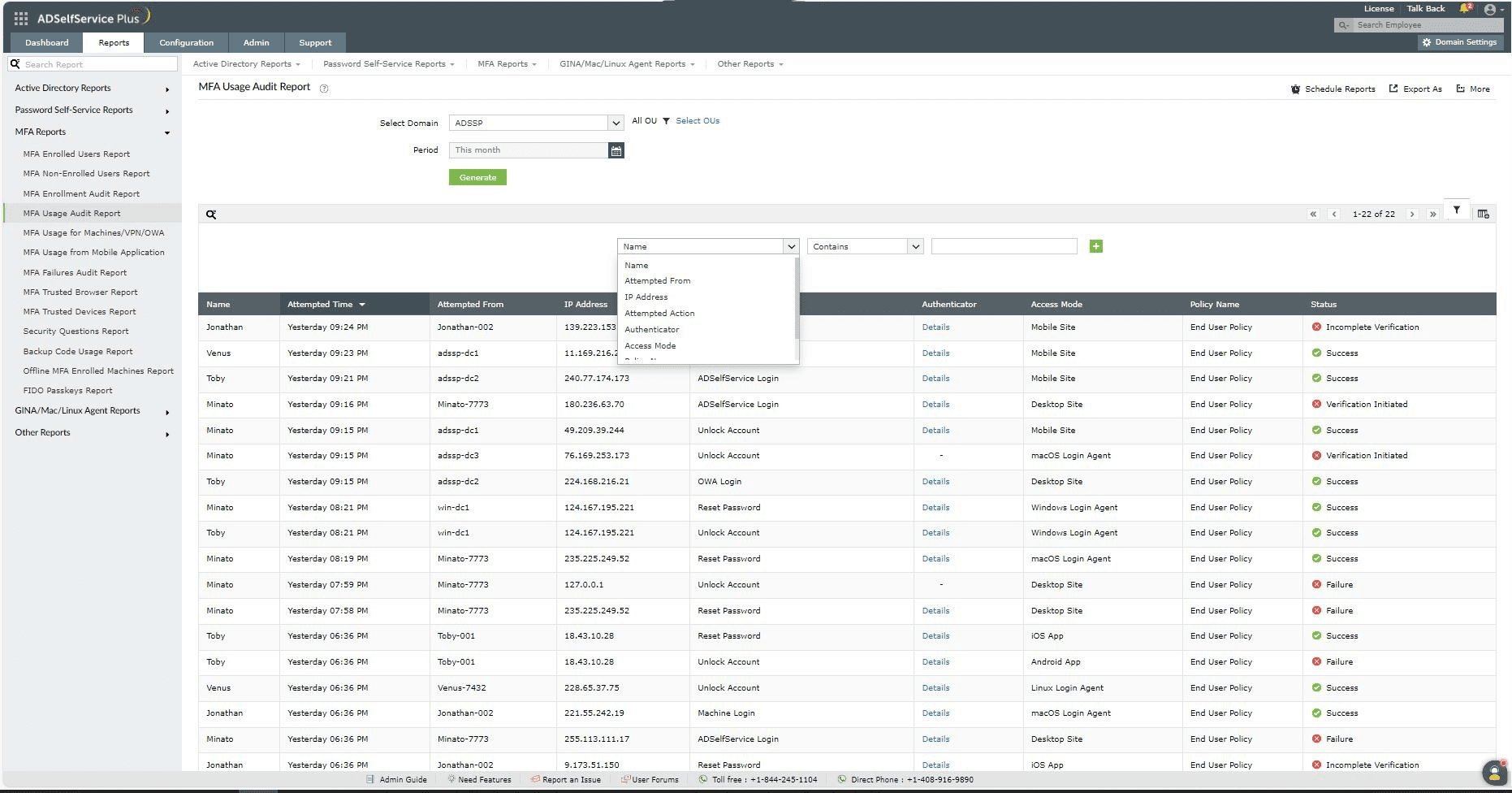
- Name: This option lets you narrow-down the MFA attempts by username. The conditions available to refine this include Contains, Does Not Contain, Equals, Is Not Equal To, Starts With, and Ends With.
- Attempted From: This option lets you display results by the name of the endpoint MFA was attempted from. The conditions available to refine this include Contains, Does Not Contain, Equals, Is Not Equal To, Starts With, and Ends With.
- IP Address: This option lets you display results by IP address. The conditions available to refine this include Contains, Does Not Contain, Equals, Is Not Equal To, Starts With, and Ends With.
- Attempted Action:The report entries can be narrowed-down based on the MFA action attempted or excluding a certain action. The actions available to refine this include ADSelfService Login, Machine Login, OWA Login, Reset Password, SSO Application Login, and more.
- Authenticator: Click on Details in the Authenticator column to display all the authenticators used for the MFA attempt, including each of their MFA statuses.
- Access Mode: The report entries can be narrowed based on the type of device MFA was attempted from. You can generate it by specifying or excluding a particular device type.
- Policy Name: This option lets you narrow-down the MFA attempts by policy name. The conditions available to refine this include Contains, Does Not Contain, Equals, Is Not Equal To, Starts With, and Ends With.
- Status: Entries can be narrowed-down by whether MFA was a Success or a Failure, or if MFA was Incomplete.
Sorting
Click any of the columns (except the Status column) to view the report's entries in ascending or descending order.
Searching
- Click on the search icon[
 ] in order to search for specific data in the report.
] in order to search for specific data in the report.
- Specific users can be searched for using their username, Policy Name, Attempted from, IP Address and type of endpoint MFA was Attempted From.
- Searching happens using the criteria 'contains'. For example, if the username column is searched for the word "jack" , then all usernames containing the sequence "jack" will be displayed as a result.
Schedule Reports, Export As and More
- The Schedule Reports option can be used to schedule the generation of reports at specified intervals, and automatically email them to administrators or specific email addresses. Learn to schedule reports here.
- The Export As option at the right corner of the page helps export the report in CSV, PDF, XLS, XLSX, HTML and CSVDE formats.
- The More option at the right corner of the page lists the Printable View, Send Mail, and Export Settings options.
- The Printable View option can be used to preview and print the report.
- The Send Mail option can be used to mail the report to the desired email addresses.
- Additionally, you can configure custom Export Settings, such as a personalized title for the report and a header logo that you may wish to display on each page.


